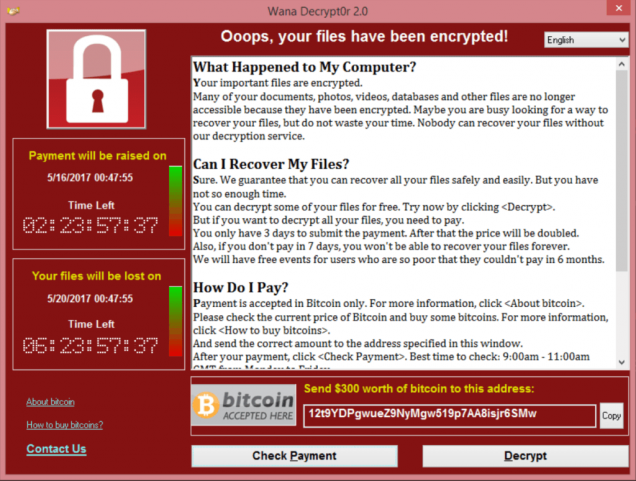
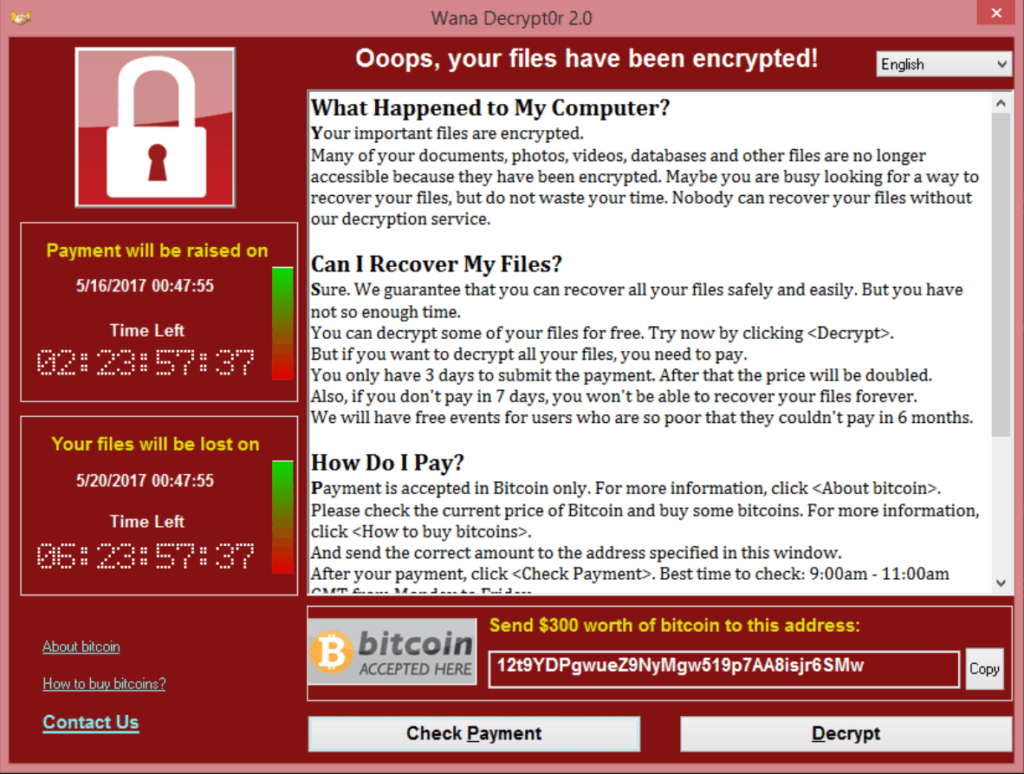
Over the last weekend, more than 200,000 computers were hit by a ransomware named WannaCry that exploits a flaw in the file sharing protocol on Windows networks. The flaw was patched in March by Microsoft with a security update, but unfortunately, not everybody installs these updates; plus, the patch did not work on Windows XP. Yes, a 16-years old operating system with no official support should not be used in critical industry like healthcare or banks, but many banks and hospitals still rely on XP. The situation was potentially so serious that Microsoft issued a security update for Windows XP, an unprecedented move.
At the moment the attack seems to have been mitigated, maybe because the infected computers have been isolated before they could spread the ransomware. Among the victims, however, there are a dozen British hospitals, the Spanish company Telefónica, FedEx and Renault, and many others.
One of the worst things about this WannaCry ransomware epidemic is that the flaw was discovered by the National Security Agency, which never warned Microsoft of this vulnerability. In fact, over the years it has taken advantage of this backdoor into networks and computers for its espionage programs. A few months ago, a group of hackers released a stock of NSA spy tools, including the one exploited by WannaCry ransomware. Only then did Microsoft realize the danger and worked hard on a security patch.
Tips to defend yourself from ransomware
Unfortunately, as of today is almost impossible to recover your data once the infection has started, even though there are attempts to block it at the start.
But computer attacks propagate according to tactics we already know: don’t visit shady sites, don’t open attachments that come from unknown contacts, always equip your PC with an antivirus and install security updates. All time.
To give us an idea
The speed and magnitude of the attack in this New York Times animation.
Animated map of how tens of thousands of computers were infected with ransomware https://t.co/voOHDugow7 pic.twitter.com/BEFeauFF3U
— The New York Times (@nytimes) 13 maggio 2017
Pretty terrifying.