
Public wireless networks: how to avoid privacy risks
There is no doubt the public WiFi is a handy tool, especially if your mobile data volume is limited. Keep it in mind: ev [...]
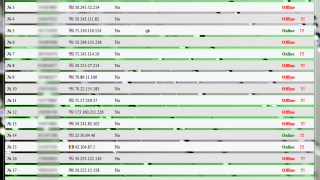
Linux.Proxy.10: A new trojan that turns Linux machines into proxy
There’s a new threat for Linux devices out there, and it is spreading pretty quickly. Its name is Linux.Proxy.10 and i [...]

Meitu, real threats behind the manga selfie app?
Surely you saw your friends faces on Facebook and Instagram with a distinctly Japanese look like they were manga charact [...]
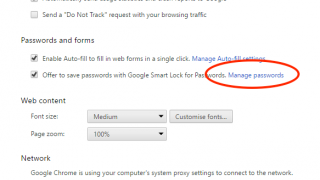
Password on Chrome: How to see those you saved
You know the feeling: you have to access a website, and you don’t remember the password you set. If you use Google Chr [...]

Backblaze 2016 report on hard disks
A cloud backup service has, more or less, the same needs we end users have: they have to buy hard disks, just like us (e [...]

Ransomware: police surveillance infected by ransomware before Trump inauguration
Botnets and malware target with pleasure connected cameras, especially in the last few months. They use them to steal pr [...]
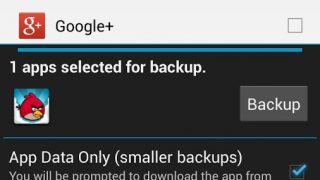
Android backup: how to do it in a few simple steps
Backing up our mobile devices is the best way to avoid the loss of our photos, music, memories, apps, important info, an [...]

Android VPN apps: be aware of the risks
A study made by several universities (Data61/CSIRO, UC Berkeley, UNSW Sydney, UCSI) found out that many Android VPN apps [...]
